High Vigilance for Global Outbreak of Computer Ransomware
2017-05-15
Event Summary
On the evening of May 12th, many college students in China reported that their computers were attacked by malicious viruses and their documents were encrypted. The source comes from the dark web, and the attack has compatibility and multilingual support, affecting multiple industries. Domestic ATMs, train stations, self-service terminals, postal services, hospitals, government service terminals, and video surveillance may all be attacked. According to reports, PetroChina gas stations in many parts of the country are unable to make online payments and can only make cash payments. The relevant person in charge of PetroChina expressed suspicion of being attacked by a virus, and the specific situation is still under investigation. As of now, some public security systems have been hacked. Common files such as documents and image materials in the recruitment system are encrypted by viruses, which then charge users a high amount of Bitcoin ransom. The virus uses RSA asymmetric algorithm, and without a private key, files cannot be decrypted.
There are two main phenomena of winning the bid:
1. A Bitcoin dialog box pops up in the user system of China National Recruitment Corporation;
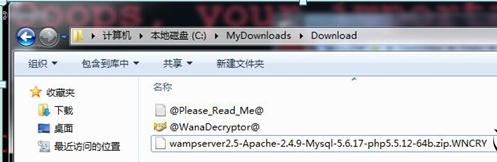
On the evening of May 12th, many college students in China reported that their computers were attacked by malicious viruses and their documents were encrypted. The source comes from the dark web, and the attack has compatibility and multilingual support, affecting multiple industries. Domestic ATMs, train stations, self-service terminals, postal services, hospitals, government service terminals, and video surveillance may all be attacked. According to reports, PetroChina gas stations in many parts of the country are unable to make online payments and can only make cash payments. The relevant person in charge of PetroChina expressed suspicion of being attacked by a virus, and the specific situation is still under investigation. As of now, some public security systems have been hacked. Common files such as documents and image materials in the recruitment system are encrypted by viruses, which then charge users a high amount of Bitcoin ransom. The virus uses RSA asymmetric algorithm, and without a private key, files cannot be decrypted.
There are two main phenomena of winning the bid:
1. A Bitcoin dialog box pops up in the user system of China National Recruitment Corporation;

2. The user files are encrypted with the suffix "wncry".
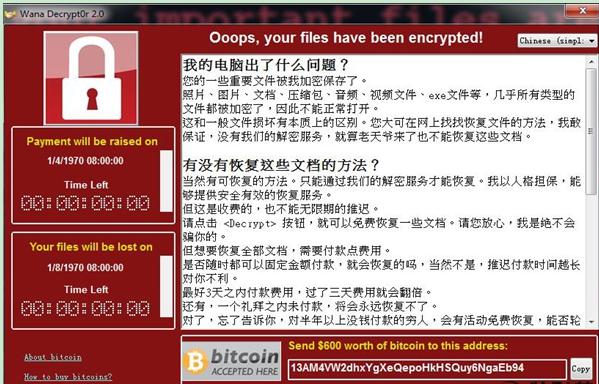

The software launched a virus attack using the Eternal Blue, which was leaked from the US Security Agency's hacker arsenal. The remote exploitation of code is related to the use of hacker toolkits by Equation Group, as announced by the hacker organization Shadow Brokers on April 14th. The ETernaLBLUE module is an SMB vulnerability exploiter that can attack Windows machines with port 445 open, enabling remote command execution. Worm software exploits server vulnerabilities and infiltrates unpatched Windows XP versions of computers through 2008 R2, achieving large-scale and rapid propagation. Once a computer in your organization is attacked, the worm will quickly search for other vulnerable computers and launch an attack.
Disposal measures
Step 1: Immediately fix vulnerabilities and upgrade patches
Please install the MS17-010 vulnerability patch on your computer as soon as possible, website: https://technet.microsoft.com/zh-cn/library/security/MS17-010 For machines such as XP and 2003 that Microsoft no longer provides security updates, install XP and some server versions of Windows Server 2003 special security patches:
https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/ If patch upgrade is not possible at the moment, please take the following emergency measures: close ports 445, 137, 138, 139, and disable network sharing; Or use immune tools: http://dl.360safe.com/nsa/nsatool.exe
Step 2: Software self check and kill
It is recommended to directly upgrade the antivirus software virus library for detection and killing. Other auxiliary detection methods include worm terminal self inspection and killing tool download address: http://www.antiy.com/response/wannacry/ATScanner.zip
Step 3: If successful, attempt to recover the file
If unfortunately hit, you can use the 360 Le worm virus file recovery tool to try file recovery. Tool download address: https://dl.360safe.com/recovery/RansomRecovery.exe
Disposal measures
Step 1: Immediately fix vulnerabilities and upgrade patches
Please install the MS17-010 vulnerability patch on your computer as soon as possible, website: https://technet.microsoft.com/zh-cn/library/security/MS17-010 For machines such as XP and 2003 that Microsoft no longer provides security updates, install XP and some server versions of Windows Server 2003 special security patches:
https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/ If patch upgrade is not possible at the moment, please take the following emergency measures: close ports 445, 137, 138, 139, and disable network sharing; Or use immune tools: http://dl.360safe.com/nsa/nsatool.exe
Step 2: Software self check and kill
It is recommended to directly upgrade the antivirus software virus library for detection and killing. Other auxiliary detection methods include worm terminal self inspection and killing tool download address: http://www.antiy.com/response/wannacry/ATScanner.zip
Step 3: If successful, attempt to recover the file
If unfortunately hit, you can use the 360 Le worm virus file recovery tool to try file recovery. Tool download address: https://dl.360safe.com/recovery/RansomRecovery.exe